[ad_1]
The e-mail could appear real, and the hyperlink that it consists of onerous to withstand: a bundle held at customs, a notification from the financial institution a couple of bank card cost… maybe even a prize that we gained. Phishing cyberattacks are an actual risk, one which takes benefit of the weakest hyperlink within the chain: people.
The rip-off works by means of deception. The attacker creates emails or textual content messages that look just about similar to those from the corporate they’re making an attempt to impersonate, normally urging the recipient to both click on on a hyperlink or open an attachment; the previous to reap bank card or banking knowledge, the latter to introduce some sort of malicious software program into the system.
AI to escalate the assaults
Concerning the quantity and precision of the phishing assaults, prospects usually are not good. “Advances in synthetic intelligence will trigger a frenzy of identification theft,” explains Francisco Arnau, regional vp of cybersecurity agency Akamai for Spain and Portugal. “Trying ahead, we are able to count on that fixed advances in synthetic intelligence, comparable to these seen in programs like GPT-3, will make focused phishing extra compelling, scalable and customary.”
These programs enable for the era of “hundreds of thousands of e mail or textual content messages, each tailor-made to a person recipient, and each with compelling human-like qualities,” Arnau continues. This can pose a big problem to current anti-phishing applied sciences and “will make it rather more troublesome for individuals to detect suspicious messages.”
The way to shield your self in opposition to a phishing assault
The very first thing to grasp is that these assaults can goal anybody. They make no distinction between people or firms, and are launched en masse – with devastating penalties for individuals who fall for them.
The numbers are overwhelming: it’s estimated that roughly 15 billion emails of those traits are despatched day by day, of which a 3rd are opened. This system additionally accounts for 90% of all safety breaches on the earth. So how are you going to shield your self in opposition to a phishing assault?
Suspicion is your biggest ally
“While you obtain a really tempting provide, it’s higher to doubt,” explains Fernando Suárez, president of the Common Council of Official Faculties of Laptop Engineering in Spain. This skilled appeals to a very powerful safety barrier, one that may save the person from critical penalties. “A financial institution won’t ever ask us to vary the password by means of an e mail or by clicking on a hyperlink.”
Kevin Mitnick, a widely known former hacker, explains to EL PAÍS that “individuals are usually trusting until they’ve already been the victims of a cyberattack, or if they’ve been taught about the specter of phishing.”
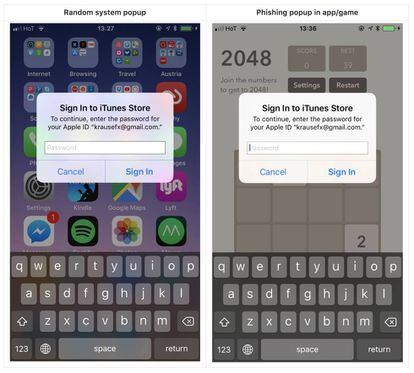
By no means click on on a hyperlink, and ask earlier than opening an attachment
All phishing assaults embody one in all two important components: both a hyperlink or an attachment. The objective of the attackers is to acquire worthwhile info from the recipient (to have their method with their checking account or bank card) or to put in malware with even worse intentions.
“In the event you obtain a hyperlink and it makes you doubt, it’s finest to sort by hand the URL of the corporate it claims to be from,” factors out Suárez, alluding to the truth that these hyperlinks are normally maliciously manipulated. The overall rule, in any case, needs to be by no means to click on on a hyperlink or open attachments that are available an e mail. For the latter, the advice is to contact the sender by different means to confirm the supply of the attachment, be it with a cellphone name, a WhatsApp message or a textual content. However by no means responding to the e-mail.
Check out the “From” discipline
Cyberattackers have gotten extra refined in terms of crafting emails, however they can not all the time camouflage them completely. One clue to detecting the deception lies within the area of origin: for those who come throughout senders with domains like “microsoft-support.com” or “apple-support.com” (just like the genuine ones, however not fairly), you’re looking at a phishing assault. In any case, and when unsure, it’s best to not work together with that e mail.
The identical applies to textual content messages, explains Suárez, who warns of a further danger: on cell phones, we’re much less cautious and act extra impulsively than on computer systems. Delivery firms are collateral victims of cyberattacks, particularly in periods of excessive exercise, comparable to Christmas. A mysterious message demanding the cost of a customs cost for a bundle might be phishing in disguise: “a financial institution or different giant entities won’t ever demand a right away cost through mobile phone,” explains Suárez. The issue isn’t a lot the cost, which is normally low, as the truth that if you make it, you’re handing your bank card info to scammers.
What time was the message despatched?
Mitnick’s expertise on this space is invaluable. The skilled supplies a telltale signal that may assist establish phishing: the time the message was despatched. Be cautious of a message despatched earlier than dawn demanding a cost or a reply. Web customers normally affiliate with environments in their very own time zone, so any exercise outdoors of it needs to be trigger for suspicion.
In the identical method, the “Topic” discipline could be a signal of an e mail’s intent: Is the language too casual? Do they tackle you by your e mail tackle as a substitute of your identify? As well as, if the topic discipline reveals a “Re:” indicating a reply to an e mail that you simply by no means despatched, you’re seeing one other camouflage approach utilized by cyber attackers.
Watch out for requests for pressing motion
One other approach hackers use when finishing up a cyberattack is conveying a way of urgency. That is evident within the messages wherein alleged delivery firms warn you that you’ve a couple of hours to pay a charge or a bundle might be returned. These sorts of firms don’t normally ship some of these messages, and in any case step one you must take on this state of affairs, if you wish to verify the veracity of the message, is to contact them by one other means.
Your guideline needs to be to “by no means click on or enter your username and password in a dialog that you simply didn’t begin; a easy rule that everybody ought to observe,” states Mitnick.
Join our weekly publication to get extra English-language information protection from EL PAÍS USA Version
[ad_2]